GoFetch: Vulnerability in M-series Mac Chips Lets Attackers Steal Encryption Keys
A vulnerability baked into Apple’s M-series of chips enables extraction of secret keys from Macs when they perform widely used cryptographic operations, academic researchers have revealed in a paper.

- "GoFetch is a microarchitectural side-channel attack that can extract secret keys from constant-time cryptographic implementations via data memory-dependent prefetchers (DMPs)."
- "The flaw - a side channel allowing end-to-end key extractions when Apple chips run implementations of widely used cryptographic protocols—can’t be patched directly because it stems from the microarchitectural design of the silicon itself."
- "Instead, it can only be mitigated by building defenses into third-party cryptographic software that could drastically degrade M-series performance when executing cryptographic operations, particularly on the earlier M1 and M2 generations."
"Basically, an attacker could trick the processor into loading secret keys into a cache and steal them from there. For that, they wouldn’t need administrator privileges. That makes the attack particularly dangerous, as any malicious application on the system could run it," explains Cybernews.
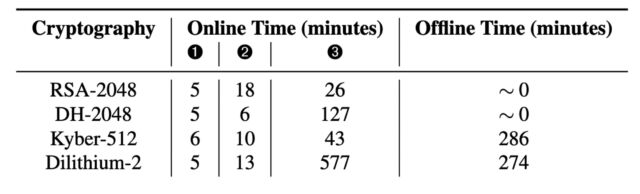
- "The GoFetch app requires less than an hour to extract a 2048-bit RSA key and a little over two hours to extract a 2048-bit Diffie-Hellman key. The attack takes 54 minutes to extract the material required to assemble a Kyber-512 key and about 10 hours for a Dilithium-2 key, not counting offline time needed to process the raw data."
- "For users, we recommend using the latest versions of software, as well as performing updates regularly. Developers of cryptographic libraries can either set the DOIT bit and DIT bit bits, which disable the DMP on some CPUs. Additionally, input blinding can help some cryptographic schemes avoid having attacker-controlled intermediate values, avoiding key-dependent DMP activation," wrote the researchers.
- "Finally, preventing attackers from measuring DMP activation in the first place, for example by avoiding hardware sharing, can further enhance the security of cryptographic protocols."
ArsTechnica Article / Archive
9toMac Article / Archive
Paper & Website




