Milk Sad: Wallet Theft Enabled By Weak Entropy
"This is the story of a wallet theft enabled by bad cryptography. It covers our research on problems with Libbitcoin Explorer 3.x (CVE-2023-39910), outlines how it is related to the Trust Wallet vulnerability (CVE-2023-31290), and shows some of the real-world impact that we were able to confirm."

- "We discovered a cryptographic weakness in the widely utilized
Libbitcoin Explorer(bx) cryptocurrency wallet tool while following up on mysterious wallet thefts. Thebx seedsubcommand for generation of new wallet private key entropy is flawed and produces insecure output."
"All versions ofbx3.0.0to3.6.0have weak entropy generation. Additionally, we have some indication that the initialsx newseedand somebx2.xversions behave insecurely on some systems. We recommend quickly moving all funds on wallets created withbx seedregardless of the original version and assuming the worst."
- "Secure cryptography requires a source of large, non-guessable numbers. If the random number generator is weak, the resulting cryptographic usage is almost always compromised. On
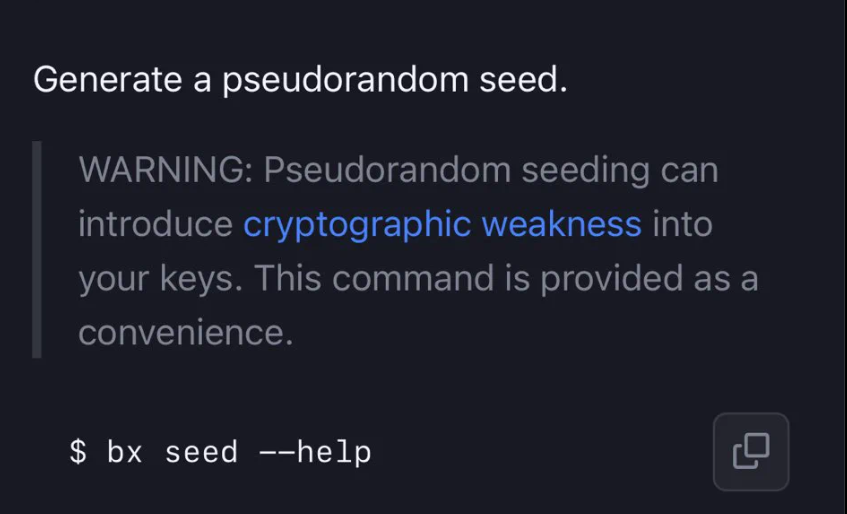
Libbitcoin Explorer3.xversions,bx seeduses the Mersenne Twister pseudorandom number generator (PRNG) initialized with 32 bits of system time." - "CVE-2023-31290 was a similar vulnerability in Trust Wallet, see Ledger Donjon’s technical writeup."
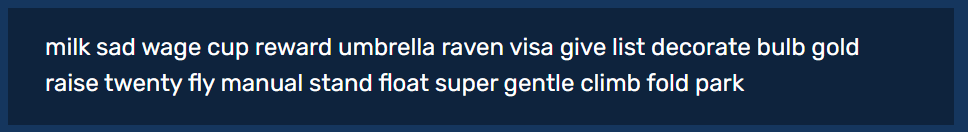
milk sadwere the first two words from the first seed phrase of this broken key generation process. Runningbx seedon3.xversions with a system time of 0.0 always generates the following secret:
- "Popular documentation like “Mastering Bitcoin” suggests the usage of
bx seedfor wallet generation."

- "Bad actors have discovered this flaw and are actively exploiting it to steal funds from affected wallets on multiple blockchains."
"We confirmed the practical use of the weak function for over 2600 cryptocurrency wallets on the Bitcoin Mainnet, and connected it to a recent large theft of cryptocurrency funds on multiple popular blockchains that amounts to an estimated $900k of damages."
- "The main theft occurred around 12 July 2023, although initial exploitation likely began at a smaller scale in May 2023. A separate but similar vulnerability in another wallet software was detected in November 2022 and actively exploited shortly after, which may be the prequel to this story."
| date | transaction | destination address | moved value | note |
|---|---|---|---|---|
| 2023-07-12 10:41 | 593e11588a2529ed.. | 3GMQRwh8Yz1WVftL.. | ~5.0538 | 14 inputs |
| 2023-07-12 10:41 | 81cfe97cc16a4939.. | 3LwDzjA1xH8amCHu.. | ~9.744 BTC | > 300 inputs |
| 2023-07-12 10:41 | a22b33a9a4ca0de2.. | 3D2mKf28exn26v7B.. | ~14.847 BTC | > 1200 inputs |
"During our accelerated coordinated disclosure to the Libbitcoin team, the Libbitcoin team quickly disputed the relevancy of our findings and the CVE assignment. By our understanding, they considerbx seeda command that should never be used productively by anybxuser since it is sufficiently documented as unsuited for safe wallet generation."
- "We have reasons to believe some
Libbitcoin Explorerversions before3.0.0also produce weakbx seedoutput in some system environments." - "I have been informed by the folks at http://distrust.co that they have filed a CVE against Libbitcoin. Apparently a wallet product used a BX command in a manner explicitly warned against. This is not a bug in BX or Libbitcoin, it is reckless wallet development," said Eric Voskuil.
- Per Ledger's CTO Charles Guillemet, "most likely very few wallets are using this."