Surveillance Firm Chainalysis Releases Report Identifying Russian Military Bitcoin Activity Then Deletes It
"We recently discovered what appears to be an example of a more direct, aggressive usage of Bitcoin for counterintelligence, through the unprecedented weaponization of the OP_RETURN field."

- Starting on February 12, 2022 — weeks before the Russian invasion of Ukraine an individual or group sent thousands of [OP_RETURN] transactions to a total of 986 unique Bitcoin addresses, claiming that these addresses were linked to Russian intelligence agencies - the Foreign Military Intelligence Agency (GRU), Foreign Intelligence Service (SVR), and Federal Security Service (FSB)."
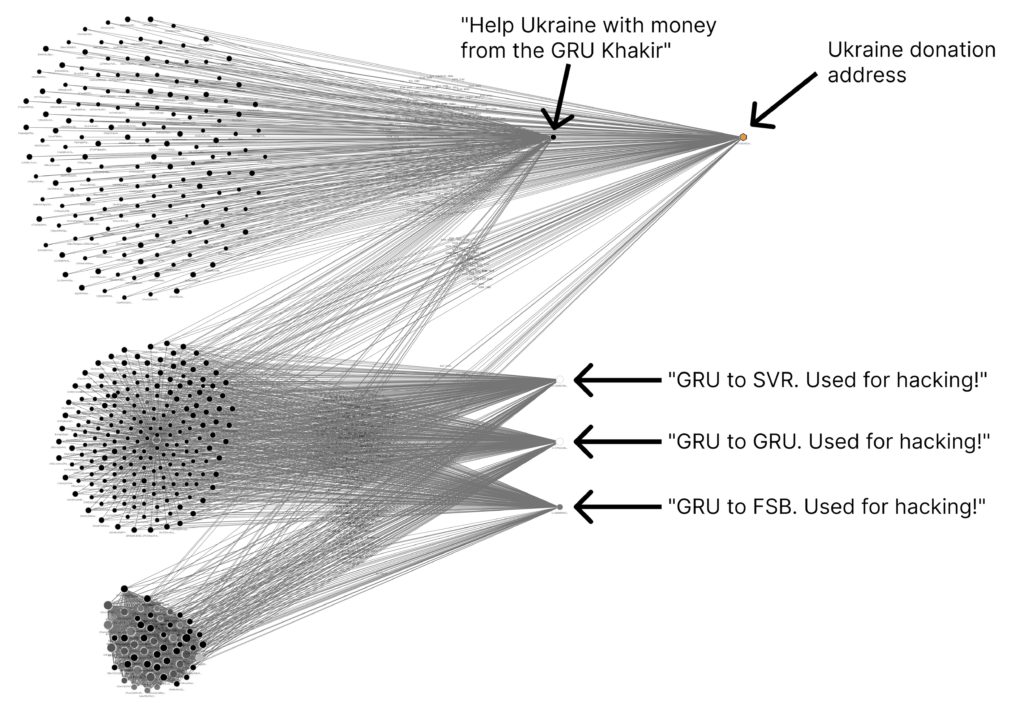
- "Assuming the vigilante’s accusations are true, that would mean this individual accessed the private keys of Russian-controlled addresses, either through hacking or collaboration with an insider."
- "We have good evidence for at least three of the addresses. Two of them — 1DLA46sXYps3PdS3HpGfdt9MbQpo6FytPm and 1L5QKvh2Fc86j947rZt12rX1EFrCGb2uPf— are referenced in a now-archived blog post from cybersecurity firm HYAS, in which the firm indicates the Russian SVR utilized the addresses to purchase infrastructure used in the infamous Solarwinds hack," while the third address appears to have been used as part of a Russian disinformation campaign when GRU covertly set up the website DCLeaks.com, and used it to publish hacked materials relating to U.S. political figures.
"An OP_RETURN marks a transaction as invalid, and effectively burns any Bitcoin included on the transaction. If one wanted to simply send a message to another person via OP_RETURN, it wouldn’t make sense to include anything more than a dust-sized amount of Bitcoin, since those funds will be rendered inaccessible."
- The OP_RETURN sender burned over $300,000 worth of bitcoin to leave these messages on-chain and started sending fundings to Ukrainian aid addresses when invasion was underway, indicating pure intentions and clarifying their support of the Ukrainian cause.
- "The possibility that the OP_RETURN sender acquired private keys for Russian-controlled addresses also suggests that the Putin regime’s crypto operations aren’t secure."
The original blog post and Twitter thread were taken down later same day without further explanation by the surveillance company.
Prior to the deletion of the posts, the story was already picked up by Coindesk, Bitcoin Magazine, and several other news outlets.




