Tails v6.11: Critical Security Fixes
Tails is a portable operating system that protects against surveillance and censorship. This release fixes several critical security vulnerabilities that were identified during an external audit by Radical Open Security. Users are urged to update to the latest version as soon as possible.

- The vulnerabilities were identified during an external security audit by Radically Open Security and responsibly disclosed to the Tails team. Users who have been using Tails a lot since January 9 without upgrading are advised to perform a manual upgrade rather than an automatic one for added safety.
"We are not aware of these attacks being used against Tails users until now. These vulnerabilities can only be exploited by a powerful attacker who has already exploited another vulnerability to take control of an application in Tails," said the project.
What's new
The update fixes the following vulnerabilities:
- Prevent an attacker from installing malicious software permanently.
- In Tails 6.10 or earlier, an attacker controlling an application could exploit a vulnerability in Tails Upgrader to install a malicious upgrade and take permanent control. A manual upgrade would erase this malicious software.
- Prevent an attacker from monitoring online activity.
- In Tails 6.10 or earlier, an attacker controlling an application can exploit vulnerabilities in others, risking deanonymization and browsing activity monitoring:
- Onion Circuits: Access and close Tor circuits.
- Unsafe Browser: Connect to the Internet without Tor.
- Tor Browser: Monitor browsing activity.
- Tor Connection: Reconfigure or block the Tor connection.
- In Tails 6.10 or earlier, an attacker controlling an application can exploit vulnerabilities in others, risking deanonymization and browsing activity monitoring:
- Prevent an attacker from changing the Persistent Storage settings.
Other changes
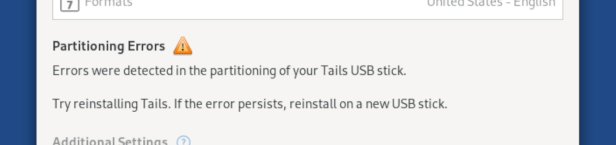
- Detection of partitioning errors. Tails USB partitions can corrupt, causing errors with Persistent Storage or upgrades due to faulty hardware, software issues, or improper removal. The software now warns earlier about these errors. If detected without Persistent Storage, it recommends reinstalling or using a new USB stick.
- Update Tor Browser to 14.0.4.
- Update Thunderbird to 128.5.0esr.
- Remove support for hardware wallets in Electrum. Trezor wallets stopped working in Debian 12 (Bookworm), and so in Tails 6.0 or later.
- Disable GNOME Text Editor from reopening on the last file.
- Add a link to the Tor Connection assistant from the menu of the Tor status icon on the desktop.
- Make it easier for our team to find useful information in WhisperBack reports.
- Do you want more? Subscribe and get No Bullshit GM report straight to your mailbox and No Bullshit Bitcoin on Nostr.
- Feedback or news tips? Drop it here.




